SEO for Cybersecurity Firms involves optimizing the online presence of cybersecurity firms, information security firms, and cyber protection companies to enhance visibility, generate qualified leads, and establish industry authority. Cybersecurity firms, which provide protection against digital threats, benefit from a tailored SEO approach that combines technical optimization, high-quality content, and strategic keyword targeting. SEO for cybersecurity firms enables them to appear in relevant search results, address specific client concerns, and differentiate from competitors in a crowded digital security market.
Implementing SEO for Information Security Firms enhances website performance through technical audits, improved site speed, structured data, and mobile optimization. Local SEO for cyber protection companies strengthens geographical visibility, which allows network security firms to attract nearby clients while maintaining a broader reach. Targeted content marketing, link building, and authority-building strategies improve trust and position firms as thought leaders in cybersecurity.
Choosing the right SEO agency is essential for cybersecurity firms to achieve measurable results. Agencies offering SEO and digital marketing services for network security firms provide customized strategies, ongoing monitoring, and continuous optimization. This ensures cybersecurity firms maintain high rankings, attract qualified leads, and sustain long-term growth in the digital security sector.
What Is a Cybersecurity Firm?
A cybersecurity firm is a specialized security company that protects businesses from digital threats by identifying vulnerabilities, which reduces risk exposure and strengthens overall security posture. A cybersecurity provider focuses on protecting networks, applications, devices, and sensitive data through threat detection, compliance alignment, and incident readiness.
A dedicated information security firm analyzes evolving attack patterns, deploys protective technologies, and delivers advisory services that help organizations make informed decisions about security priorities. This type of cyber defense company implements technical audits, secure architecture planning, and operational performance optimization to ensure environments remain safe and reliable.
Cyber defense firms integrate expertise, continuous monitoring, and strategic guidance to enhance trust, improve operational resilience, and reduce the likelihood of costly breaches. Aligning security measures with business objectives allows a cybersecurity firm to establish authority, demonstrate industry leadership, and provide measurable value for clients across sectors.
What Does SEO Mean for Cybersecurity Firms?
SEO for cybersecurity firms is the strategic process that increases visibility for cybersecurity companies in search engine results. This process allows information security firms to attract highly targeted traffic, generate qualified leads, and establish authority within the digital security domain. Search engine optimization for cybersecurity providers integrates technical website improvements, content development, and backlink acquisition to enhance credibility and performance in organic search rankings.
For a cybersecurity provider, SEO involves precise keyword targeting, which aligns the services of the firm, such as threat assessment, network protection, and incident response, with the terms potential clients use to discover solutions. Technical SEO ensures the website of the firm demonstrates security best practices, fast load times, mobile responsiveness, and a logically organized site structure that search engines crawl and index efficiently. These practices signal trustworthiness and operational reliability to prospective clients seeking security expertise.
High-quality content creation and link-building reinforce authority for cybersecurity firms. Producing detailed threat analyses, case studies, whitepapers, and compliance guides positions cyber defense companies as thought leaders. Authoritative backlinks from technology publications, partner organizations, and industry associations enhance the domain authority of a cybersecurity firm, which directly impacts ranking and discoverability.
Is SEO Truly Important for Cybersecurity Firms?
Yes, SEO is essential for cybersecurity firms because it directly increases online visibility, credibility, and qualified lead generation. For a cyber defense company, search engine optimization ensures that information security providers appear for high-intent searches, such as “managed detection and response provider” or “network threat assessment services.” High organic rankings allow cybersecurity companies to reach decision-makers actively seeking solutions, which enhances their ability to attract relevant clients.
For a cybersecurity provider, SEO builds trust and authority by signaling expertise through technical content and structured, secure websites. Publishing threat analyses, case studies, and compliance reports establishes the firm as a credible authority in the digital security domain. Organic search visibility acts as proof of capability and reliability, reinforcing the reputation of the firm among prospective clients and industry stakeholders.
Additionally, SEO delivers cost-effective, long-term advantages for cybersecurity firms. Unlike paid campaigns, optimized organic channels maintain a continuous flow of qualified leads without ongoing ad spend. Targeted content educates potential clients on cybersecurity risks and compliance requirements while differentiating the firm from competitors. Combining technical website optimization, secure protocols, and authoritative content ensures that cybersecurity firms not only rank highly but also maintain credibility and competitive positioning in a saturated market.
What Are the Advantages of Implementing SEO Strategies for Cybersecurity Firms?
The key advantages of implementing SEO strategies for cybersecurity firms include increasing online visibility, attracting qualified clients, and establishing authority in the information security domain. These benefits allow cyber defense companies and security service providers to grow efficiently while maintaining a strong reputation among enterprise clients. The key benefits of implementing SEO strategies for cybersecurity firms are listed below.
- Enhanced Online Visibility: Optimized search presence ensures cybersecurity firms appear for high-intent searches relevant to security services.
- Authority and Credibility: Publishing detailed threat analyses, case studies, and compliance resources positions the firm as a trusted security provider.
- Qualified Lead Generation: SEO attracts visitors actively searching for cybersecurity solutions, increasing the likelihood of high-value B2B inquiries.
- Cost-Efficient Long-Term Growth: Organic search traffic continues generating leads without ongoing advertising spend, reducing customer acquisition costs.
- Competitive Differentiation: Targeting niche cybersecurity keywords allows smaller firms to outrank larger competitors using generic marketing approaches.
- Improved User Trust: Secure, fast, and well-structured websites demonstrate technical competence, reinforcing client confidence in the cybersecurity firm.
- Educational Authority: SEO-driven content educates prospects on cyber threats, compliance needs, and protective solutions, establishing thought leadership.
- Measurable Performance Insights: Analytics tracking keyword rankings, traffic, and conversions provides actionable intelligence for optimizing security marketing strategies.
These advantages combine to make SEO an irreplaceable strategy for cybersecurity firms, information security companies, and cyber defense providers seeking long-term visibility, credibility, and growth in competitive markets.
Is SEO for Cybersecurity Companies Different from SEO for IT Companies?
Yes, SEO for cybersecurity companies differs from SEO for general IT companies due to the specialized nature of security services, compliance requirements, and high-stakes decision-making by enterprise clients. Cybersecurity firms target technical keywords such as “endpoint detection solutions” or “managed detection and response provider,” whereas IT companies often focus on broader terms like “IT consulting” or “network services.”
Content strategy for cybersecurity firms emphasizes trust, authority, and risk mitigation. Publishing case studies on threat prevention, compliance guides for HIPAA or GDPR, and detailed security whitepapers ensures prospects perceive the firm as an expert and reliable. In contrast, an IT company SEO often prioritizes service over trust-building content.
Technical SEO requirements also vary. Cybersecurity firm websites must demonstrate strong security measures (HTTPS, fast performance, secure forms) as a trust signal, while IT company websites prioritize usability and service presentation. Link-building strategies for cybersecurity focus on high-authority industry publications, research citations, and regulatory references, differing from IT companies that often pursue broader technology or business directories. These distinctions make cybersecurity SEO a more specialized, high-trust process compared to general IT SEO.
How Can Cybersecurity Firms Get Started with SEO Effectively?
To get started effectively with SEO, cybersecurity firms should focus on technical site optimization, on-page content strategy, authoritative link building, and continuous performance tracking. Implementing a structured approach ensures higher visibility in search engines (Google, Bing, Yahoo!), establishes trust, and drives qualified leads. Each SEO step must align with the security expertise, client needs, and compliance requirements of the firm.
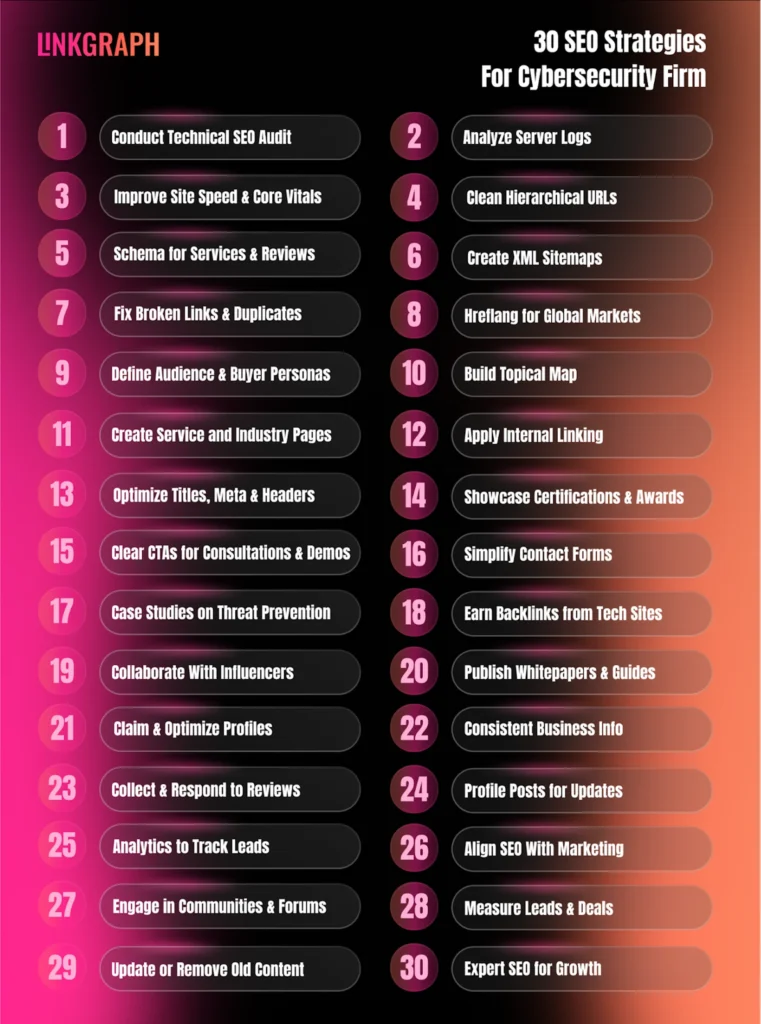
There are 30 SEO strategies for cybersecurity firms. The 30 SEO strategies for cybersecurity firms are listed below.
- Conduct a Technical SEO Audit to Identify Security and Crawl Issues
- Analyze Server Logs to Understand How Search Engines Access Your Site
- Improve Site Speed and Core Web Vitals for a Secure, Fast Experience
- Use Clean, Hierarchical URL Structures for Easy Navigation
- Implement Schema Markup for Organization, Services, and Reviews
- Create XML Sitemaps for Pages, Resources, and Media
- Fix Broken Links, Redirects, and Duplicate Content Issues
- Use Hreflang Tags for Targeting International Cybersecurity Markets
- Define Target Audience, Market Gaps, and Buyer Personas
- Construct a Topical Map Based on Your Source Context
- Create Pages for Key Services and Industry-Specific Solutions
- Internally link Pages Strategically Following Root, Seed, Node Hierarchy
- Optimize Titles, Meta Descriptions, Headers, and Image Alt Text
- Showcase Certifications, Awards, Partnerships, and Security Credentials
- Add Clear CTAs for Consultations, Security Audits, or Demo Requests
- Simplify Contact Forms and Inquiry Processes for Higher Conversions
- Publish Case Studies Highlighting Threat Prevention and Compliance Success
- Earn Backlinks From Reputable Cybersecurity, IT, and Tech Websites
- Collaborate With Industry Associations, Partners, and Influencers
- Publish Whitepapers, Security Guides, and Threat Research Articles
- Claim, Optimize, and Verify Business Profiles on Google, Bing, and Industry Directories
- Ensure Consistent Business Information Across All Listings
- Collect and Respond to Client Reviews to Build Credibility
- Use Business Profile Posts to Announce Security Updates or Services
- Set Up Analytics Tools to Track Traffic, Leads, and Conversions
- Align SEO Goals With Marketing and Lead Generation Objectives
- Engage With Cybersecurity Communities, Forums, and Professional Networks
- Measure Success by Qualified Leads, Client Inquiries, and Closed Deals
- Update, Consolidate, or Remove Outdated Page Content
- Consider Expert SEO Support for Continuous Optimization and Growth
Each step builds a comprehensive SEO framework that strengthens technical performance, enhances user experience, and positions the firm as a trusted cybersecurity authority. Continuous evaluation and refinement ensure the strategy aligns with market changes and evolving security threats. We have broken down the 30 SEO strategies for cybersecurity firms below.
1. Conduct a Technical SEO Audit to Identify Security and Crawl Issues
A technical SEO audit identifies weaknesses that restrict the visibility and stability of a website. For cybersecurity firms, it verifies whether search engines properly crawl, render, and index pages without encountering security or performance barriers. This step strengthens search presence and reinforces technical reliability, both essential in a field built on trust and precision.
Start by reducing server response time below 100 milliseconds, since slow servers increase crawl delays and harm user experience. Search engines allocate limited crawl budgets, so speed directly affects how efficiently new or updated pages appear in search results. Next, confirm that HTML crawl requests exceed 95%, since this metric shows whether crawlers access core content rather than being diverted by scripts or blocked resources.
Maintain a refresh rate around 20%, which indicates steady re-crawling of essential pages without overloading the server. A discovery rate of 7–8% ensures that new pages or updated resources enter the crawl cycle regularly, improving visibility for fresh content. Finally, perform a log file analysis using enterprise-level SEO monitoring tools to locate areas where crawl budget is wasted, such as redirect chains, orphan pages, or outdated URLs. Adjusting these parameters strengthens index coverage, improves ranking stability, and projects the technical excellence expected from a cybersecurity provider.
2. Analyze Server Logs to Understand How Search Engines Access Your Site
Server log analysis examines how search engines navigate the website of a cybersecurity firm, highlighting crawl patterns, page requests, and indexing behavior. Understanding these interactions strengthens technical SEO and ensures that important pages receive priority attention. For cybersecurity firms, which often have secured or restricted content areas, this strategy ensures search engines focus on indexable, high-value pages that drive qualified traffic.
Analyzing log files identifies pages that receive frequent crawls, pages ignored by search engines, and areas where crawl budget is wasted. Observing response codes, page requests, and user-agent activity highlights broken links, redirect loops, or unoptimized page structures that reduce indexing efficiency. This strategy provides actionable insights for optimizing site architecture and aligning it with search engine priorities.
Implementing improvements based on server log insights enhances indexing speed, ensures critical content is discoverable, and strengthens overall site visibility. Cybersecurity firms benefit from increased organic exposure, higher search rankings for targeted security solutions, and improved technical authority that signals trustworthiness to search engines.
3. Improve Site Speed and Core Web Vitals for a Secure, Fast Experience
Optimizing site speed and Core Web Vitals enhances the browsing experience while strengthening technical SEO for cybersecurity firms. Fast-loading pages, minimal layout shifts, and quick interactivity ensure visitors engage effectively with service offerings, demonstrating professionalism and reliability. For firms handling sensitive security information, site performance signals trustworthiness and operational excellence to potential clients.
Core Web Vitals focus on three key metrics: Largest Contentful Paint (LCP), which measures page loading speed; First Input Delay (FID), which tracks interactivity; and Cumulative Layout Shift (CLS), which monitors visual stability. Improving these metrics reduces bounce rates, increases session duration, and boosts search engine rankings, ensuring high-priority security pages appear prominently in results. Techniques include optimizing server response times, compressing resources, and refining front-end elements without compromising security protocols.
Enhancing site speed and Core Web Vitals delivers measurable SEO benefits, including improved indexing efficiency and higher visibility for critical service pages. Firms that maintain fast, stable, and secure websites experience stronger organic traffic, elevated user trust, and increased conversion rates for cybersecurity solutions.
4. Use Clean Hierarchical URL Structures for Easy Navigation
Implementing clean, hierarchical URL structures strengthens technical SEO and enhances the user experience for cybersecurity firms. Logical URL hierarchies make it easier for search engines to crawl and index service pages while allowing visitors to navigate complex security offerings efficiently. Well-structured URLs communicate page relationships, highlighting primary services, sub-services, and supporting content.
A hierarchical structure starts with the homepage, followed by category pages, subcategory pages, and individual service or resource pages. For example, a main security service page follow the pattern: /services/network-security/firewall-implementation/. Such structuring clarifies content relationships, improves crawl efficiency, and emphasizes high-value pages to search engines. Consistent naming conventions, lowercase letters, and hyphenated words further enhance readability and indexing.
Optimizing URL hierarchies delivers measurable benefits, including faster indexing, stronger internal linking, and improved organic rankings for targeted security services. Cybersecurity firms that maintain clear, intuitive URLs experience higher user engagement, reduced navigation errors, and increased discoverability of specialized solutions in search results.
5. Implement Schema Markup for Organization Services and Reviews
Adding schema markup enhances technical SEO for cybersecurity firms by providing structured data that search engines interpret efficiently. Structured data communicates specific information about the organization, individual services, and client reviews, allowing search engines to display rich snippets in search results. Rich snippets improve visibility, click-through rates, and perceived credibility for specialized security services.
Cybersecurity firms should implement an organizational schema to define the company name, logo, contact details, and location. Service schema highlights each security offering, including detailed descriptions, pricing tiers, and service categories. Review schema captures client testimonials, star ratings, and feedback dates, signaling authority and trustworthiness. These structured data elements allow search engines to index content more precisely and present accurate information to potential clients.
Effective schema implementation boosts search performance, drives higher-quality traffic, and strengthens brand authority. Proper markup enables enhanced results like featured snippets, service listings, and review stars, which increase user confidence and encourage engagement. Cybersecurity firms gain measurable advantages in visibility and ranking signals by maintaining a comprehensive, accurate schema across all service pages.
6. Create XML Sitemaps for Pages, Resources, and Media
XML sitemaps strengthen technical SEO for cybersecurity firms by providing search engines with a clear roadmap of all website content. Sitemaps enable search engines to discover, index, and prioritize pages, resources, and media efficiently, ensuring that critical service pages and security resources are visible in search results. Properly structured sitemaps reduce crawl errors and improve overall site indexation.
Cybersecurity firms should generate separate sitemaps for standard pages, downloadable resources such as PDFs or whitepapers, and media files, including images and videos. Each sitemap should list URLs with accurate metadata, such as last modified dates and content type. Linking these sitemaps in the robots.txt file of a website and submitting them to search engines allows crawlers to access every important page and asset systematically.
Maintaining compact and organized sitemaps enhances crawl efficiency, prevents duplicate indexing, and ensures that newly published content is indexed quickly. Firms expect improved search visibility, faster updates in search results, and a more accurate representation of services and resources for potential clients.
7. Fix Broken Links, Redirects, and Duplicate Content Issues
Broken links, improper redirects, and duplicate content negatively impact technical SEO for cybersecurity firms by creating crawl errors and reducing user trust. These issues prevent search engines from properly indexing pages and lower rankings for critical service and resource pages. Correcting these problems ensures that both search engines and potential clients access the intended content without disruption.
Cybersecurity firms should conduct comprehensive site audits to identify broken links, redirect chains, and duplicate pages. Each broken link should either be removed or replaced with a functional URL. Redirects must follow proper hierarchy, preferably using permanent redirects for moved content, to preserve link equity. Duplicate content should be consolidated using canonical tags or merged into authoritative pages that accurately represent the service or solution.
Resolving these technical issues improves crawl efficiency, strengthens domain authority, and enhances user experience by providing seamless navigation. Firms expect higher rankings for key services, better indexation of critical security content, and reduced bounce rates from frustrated visitors encountering errors or repetitive pages.
8. Use Hreflang Tags for Targeting International Cybersecurity Markets
Hreflang tags indicate language and regional targeting for international versions of a website, which enhances SEO for cybersecurity firms operating globally. These tags allow search engines to serve the correct page version to users based on their language preferences and location. Proper implementation ensures that content reaches the intended audience and avoids duplicate content penalties across regions.
Cybersecurity firms should map all international pages and specify language and region codes in hreflang attributes. Each page should reference all relevant language versions, including itself, to establish a complete tag set. Tags be added in the HTML header, XML sitemaps, or HTTP headers, depending on site structure and scale. Firms should regularly audit these tags to confirm accuracy and prevent errors that misdirect search engines.
Correct use of hreflang tags improves global visibility, ensures search engines display the right content to target audiences, and enhances organic traffic from international markets. Firms expect better engagement, higher conversions from localized visitors, and stronger authority in multiple geographic regions.
9. Define Target Audience, Market Gaps, and Buyer Personas
Defining the target audience, identifying market gaps, and creating buyer personas establishes the foundation for effective SEO for cybersecurity firms. A well-defined audience clarifies which organizations, industries, and decision-makers require cybersecurity solutions, while market gap analysis highlights areas with unmet demand or underserved niches. Understanding these elements ensures content and service offerings align precisely with client needs and expectations.
Cybersecurity firms should segment audiences by company size, industry, security requirements, and decision-maker roles. Market research, competitor analysis, and user behavior insights identify gaps where content, tools, or services are lacking. Buyer personas synthesize this information into representative profiles, specifying goals, challenges, and preferred content formats. This step directly informs the creation of topical maps, which organize content hierarchically and link relevant subjects across pages. Topical maps guide the internal linking structure, ensuring that each page addresses specific audience intent while reinforcing authority in specialized cybersecurity topics.
Accurate audience definition and gap analysis improve content relevance, enhance organic rankings, and attract qualified leads. Firms implementing these practices see better alignment between search intent and available solutions, increased engagement, and more efficient SEO performance through precise topical mapping.
10. Construct a Topical Map Based on Your Source Context
Constructing a topical map organizes the content ecosystem of a cybersecurity firm, connecting primary service pages, related resources, and informative articles in a hierarchical structure. Topical maps ensure that each page focuses on specific security solutions, compliance standards, or threat mitigation strategies, while logically linking related content to improve discoverability. This approach strengthens authority in specialized cybersecurity areas and guides search engines through the content hierarchy of a site.
The process begins with analyzing existing content and identifying core topics, subtopics, and associated keywords. Source context from competitor research, industry trends, and client queries informs the creation of clusters that reflect real user intent. Primary nodes represent key services like threat detection or managed security, while secondary nodes cover related guides, FAQs, and case studies. Internal links between nodes reinforce topical relevance and enable search engines to understand page relationships.
Implementing a well-structured topical map increases page indexation, improves ranking for long-tail keywords, and enhances user navigation. Cybersecurity firms leveraging these maps experience higher engagement, better content authority, and a clear pathway for expanding future content clusters.
11. Create Pages for Key Services and Industry-Specific Solutions
Creating dedicated pages for key cybersecurity services and industry-specific solutions establishes a clear, organized website structure that enhances relevance for both users and search engines. Each page should focus on a particular offering, such as managed detection, endpoint protection, or compliance consulting, while highlighting the expertise and differentiators of a firm. These pages act as primary entry points for potential clients seeking targeted security solutions.
On-page SEO principles guide the construction of these pages. Titles, headers, meta descriptions, and content must reflect precise keywords related to each service, ensuring alignment with user intent. Including detailed descriptions, benefits, and actionable information reinforces authority and informs decision-makers. Integrating multimedia elements such as diagrams, process flows, or brief instructional content increases engagement while keeping the page informative and digestible.
Well-structured service pages improve internal linking opportunities, allowing topical maps to connect primary pages with related content like case studies, guides, or industry insights. The result is higher indexing efficiency, improved rankings for niche security keywords, and a smooth user experience that encourages conversions.
12. Internally Link Pages Strategically Following Root Seed Node
Internal linking structures organize a cybersecurity website by guiding search engines and users through a clear hierarchy. The root page represents the homepage or main pillar, seed pages cover major service categories, and node pages focus on specific topics or sub-services. This structure ensures that authority flows from high-level pages to detailed content, improving crawl efficiency and page ranking.
On-page SEO practices dictate how links are placed contextually within content. Anchor text should reflect the targeted keyword or concept, connecting primary services with relevant pages. For example, a seed page on “endpoint security solutions” links to nodes like “advanced malware detection” or “remote device protection,” creating a logical content network that search engines easily index.
Strategic internal linking enhances discoverability, reinforces topical relevance, and signals authority across related pages. This approach increases the likelihood of ranking for both primary and niche cybersecurity keywords while guiding visitors naturally through the site, improving engagement and potential conversions for high-intent clients.
13. Optimize Titles, Meta Descriptions, Headers, and Image Alt Text
Optimizing titles, meta descriptions, headers, and image alt text defines how each page communicates its purpose to search engines and visitors. Titles should include primary keywords relevant to cybersecurity services, while meta descriptions summarize content in a concise, actionable format that encourages clicks. Headers organize content hierarchically, guiding search engines to interpret page structure and relevance accurately. Image alt text conveys context for visuals, increasing accessibility and reinforcing keyword signals.
This on-page SEO strategy improves indexing precision and aligns content with search intent. For instance, a page targeting “endpoint security solutions” should include the keyword in the title, main headers, and alt text of supporting images. Consistent optimization strengthens visibility, click-through rates, and engagement metrics, which signals search engines that the website provides relevant, authoritative content for technical audiences.
Performing regular audits of metadata, headers, and alt text identifies gaps or duplication that reduce performance. Updating these elements maintains alignment with evolving search queries, increases relevance for cybersecurity topics, and enhances organic rankings over time.
14. Showcase Certifications Awards Partnerships and Security Credentials
Displaying certifications, awards, partnerships, and security credentials establishes authority and credibility for a cybersecurity firm. Certifications like CISSP or ISO 27001, industry awards, and strategic partnerships signal expertise and reliability to clients and search engines. Highlighting these credentials across service pages, landing pages, and about sections ensures potential clients perceive the firm as trustworthy and competent.
This on-page SEO strategy reinforces user confidence and improves engagement metrics such as time on page and conversion rates. Search engines interpret prominently displayed credentials as signals of expertise and authority, which positively influence rankings. For example, featuring an ISO 27001 certification on an endpoint security service page communicates both technical capability and compliance adherence.
Maintaining an up-to-date showcase of awards, certifications, and partnerships strengthens brand reputation. Updating pages with newly earned credentials or notable collaborations ensures continuous reinforcement of expertise, improves discoverability for relevant searches, and strengthens long-term authority in the cybersecurity niche.
15. Add Clear CTAs for Consultations, Security Audits, or Demo Requests
Clear calls-to-action (CTAs) guide visitors toward taking specific actions, such as requesting a consultation, scheduling a security audit, or signing up for a product demo. Well-designed CTAs use concise, action-oriented text and are strategically placed on service pages, landing pages, and blog posts to capture high-intent prospects.
This on-page SEO strategy improves user interaction metrics, including click-through rates and conversion rates, which indirectly influence search engine rankings. For example, placing a “Request Security Audit” button near a detailed service description encourages users to take immediate action while signaling engagement to search engines.
Optimizing CTA placement, color contrast, and wording ensures that each page effectively drives conversions. Regularly testing and refining CTAs based on user behavior strengthens lead generation, enhances the effectiveness of marketing campaigns, and aligns the website structure with business goals for recurring cybersecurity services.
16. Simplify Contact Forms and Inquiry Processes for Higher Conversions
Simplifying contact forms and inquiry processes reduces friction and increases submission rates for cybersecurity firms. Short, clearly labeled fields, minimal required information, and logical flow improve the chances that high-intent visitors complete their inquiry.
Streamlined forms enhance user experience while sending positive engagement signals to search engines, which influences rankings and authority. A concise “Request Consultation” or “Schedule Security Audit” form encourages qualified leads to interact without abandonment.
Implementing multi-step forms, progress indicators, and clear validation improves usability and data accuracy. Regular audits to remove unnecessary fields, maintain efficiency, and ensure forms align with broader lead generation and conversion objectives. These changes directly increase inquiries, foster trust, and connect site interactions to measurable business outcomes.
17. Publish Case Studies Highlighting Threat Prevention and Compliance Success
Publishing detailed case studies allows cybersecurity firms to demonstrate expertise and practical results in threat prevention and regulatory compliance. Case studies illustrate real-world applications of security solutions, showing how a firm mitigates risks and addresses industry-specific challenges. They act as authoritative content that reassures potential clients about the capabilities and reliability of a firm.
High-quality case studies influence both user trust and search engine perception. They provide keyword-rich, in-depth content that aligns with client search intent, covering topics such as ransomware mitigation, SOC implementation, or GDPR compliance. Structuring case studies with problem-solution-outcome frameworks allows firms to signal experience and authority, which strengthens search relevance and organic rankings.
Firms should include measurable results, client testimonials, and actionable insights within the case study content to make it more effective and credible. Linking these pages internally to related service offerings amplifies topical relevance and discoverability. Regularly updating case studies ensures accuracy, improves engagement metrics, and attracts high-intent leads who are more likely to convert.
18. Earn Backlinks From Reputable Cybersecurity IT and Tech Websites
Earning backlinks from authoritative cybersecurity, IT, and technology websites strengthens the domain authority of a firm and improves search engine visibility. Backlinks act as endorsements that signal credibility, relevance, and expertise to search engines while directing qualified referral traffic to the website.
High-quality backlinks increase trustworthiness in competitive cybersecurity markets. Firms that secure mentions or links from industry publications, partner websites, or professional associations position themselves as recognized authorities in areas such as threat intelligence, compliance, or network security. Consistent acquisition of these links enhances organic rankings for targeted keywords and increases visibility for specialized services.
Cybersecurity firms should focus on outreach strategies targeting industry-specific content platforms, guest posting opportunities, and digital press releases to implement effectively. Tracking backlink profiles ensures that links remain relevant and authoritative. Over time, a strong backlink portfolio contributes to sustainable SEO growth, attracts decision-makers seeking specialized solutions, and reinforces the expertise of a firm within the global cybersecurity ecosystem.
19. Collaborate With Industry Associations, Partners, and Influencers
Collaborating with industry associations, strategic partners, and cybersecurity influencers enhances brand authority and expands the reach of the firm across relevant networks. Partnerships with recognized organizations or thought leaders signal expertise and credibility to both search engines and potential clients, increasing the perceived value of the services offered.
These collaborations provide access to high-quality link opportunities, joint content initiatives, and co-branded resources such as webinars, research reports, or educational guides. Engaging with industry associations allows cybersecurity firms to align their messaging with trusted entities while influencers amplify content visibility across professional and social channels, creating referral traffic and generating qualified leads.
Implementation involves identifying authoritative partners and influencers within cybersecurity, establishing mutually beneficial content or event collaborations, and maintaining consistent engagement. Over time, these collaborations strengthen organic search performance, increase visibility for niche security solutions, and establish the firm as a thought leader in specialized cybersecurity domains.
20. Publish Whitepapers, Security Guides, and Threat Research Articles
Publishing whitepapers, security guides, and threat research articles establishes a cybersecurity firm as an authoritative source in the industry. These resources provide in-depth insights into emerging threats, best practices, and compliance strategies, attracting high-intent visitors seeking expert information.
High-quality content like whitepapers and technical guides earns natural backlinks from industry publications, partners, and educational platforms. Sharing threat research and case studies demonstrates expertise, builds trust with potential clients, and improves organic search rankings by signaling authority and relevance to search engines.
Implementation involves identifying critical security topics, producing detailed and actionable documents, and distributing them across websites, newsletters, and professional networks. Cybersecurity firms should optimize content with structured data, clear headings, and targeted keywords. Over time, these publications increase lead generation, enhance brand credibility, and strengthen visibility in search results for highly competitive, niche cybersecurity queries.
21. Claim Optimize and Verify Business Profiles on Google, Bing, and Industry Directories
Claiming, optimizing, and verifying business profiles on search engines and industry directories ensures that a cybersecurity firm appears accurately across digital platforms. Verified profiles increase visibility in local and global searches, making it easier for potential clients to find specific cybersecurity services, such as threat detection or compliance audits.
Optimization involves completing all profile fields with consistent business information, adding service descriptions, high-quality images, certifications, and links to the website of the firm. Providing accurate categories and contact details improves search engine trust and local ranking signals. Profiles also act as gateways for collecting reviews, promoting updates, and highlighting credentials, which reinforce credibility with prospective clients.
Regular maintenance of these profiles allows cybersecurity firms to track engagement, monitor user interactions, and update offerings promptly. Consistent, optimized listings contribute to higher organic visibility, stronger trust signals, and increased qualified leads from both local and industry-specific search queries.
22. Ensure Consistent Business Information Across All Listings
Maintaining consistent business information across all online listings ensures that a cybersecurity firm presents a unified digital identity. Accurate details such as business name, address, phone number, services, and website URL enable search engines to associate the firm with authoritative, reliable data, improving ranking for relevant security-related queries.
Consistency reduces confusion for potential clients seeking services like managed detection, endpoint protection, or compliance audits. Discrepancies across directories, social platforms, and industry databases fragment authority, dilute trust signals, and negatively affect local SEO performance. Firms should regularly audit listings, verify updates, and correct mismatched or outdated information.
A coherent presence across platforms enhances discoverability, reinforces credibility, and increases lead generation opportunities. Cybersecurity firms that maintain accurate, synchronized listings experience better organic visibility, improved local search rankings, and stronger brand recognition within competitive security markets.
23. Collect and Respond to Client Reviews to Build Credibility
Collecting and responding to client reviews establishes the authority and reliability of a cybersecurity firm in the marketplace. Positive feedback on services such as penetration testing, compliance consulting, or incident response signals expertise to both search engines and potential clients.
Active review management allows firms to address concerns, clarify service capabilities, and demonstrate responsiveness. Timely responses to reviews highlight professionalism and attentiveness, increasing trust among prospective clients evaluating cybersecurity providers. Soliciting reviews from verified clients ensures authenticity and strengthens the reputation of the firm.
Consistent engagement with client feedback improves search visibility for local and industry-specific queries. Firms that prioritize review collection and responses experience higher organic rankings, stronger credibility, and increased client acquisition, reinforcing long-term growth in the competitive cybersecurity sector.
24. Use Business Profile Posts to Announce Security Updates or Services
Business profile posts allow cybersecurity firms to communicate important updates, service launches, or security advisories directly to their audience. Posting regularly about new offerings, such as managed detection services, compliance audits, or vulnerability assessments, signals activity and reliability to search engines and prospective clients.
Firms leverage these posts to highlight achievements, certifications, or partnerships, demonstrating expertise and maintaining engagement. Well-crafted announcements improve user interaction and encourage visits to key service pages, reinforcing the visibility and authority of the firm.
Active use of business profile posts strengthens local and industry-specific SEO presence. Firms that maintain timely updates increase discoverability, showcase credibility, and drive traffic to conversion-focused pages, ultimately enhancing client acquisition and retention within the cybersecurity market.
25. Set Up Analytics Tools to Track Traffic Leads and Conversions
Analytics tools provide cybersecurity firms with insights into website performance, user behavior, and campaign effectiveness. Tracking metrics such as sessions, bounce rates, page views, and conversion paths allows firms to measure the impact of SEO strategies on lead generation and client acquisition.
Proper configuration ensures firms capture data from key touchpoints, including service pages, contact forms, and demo request submissions. This data identifies high-performing pages, potential drop-off points, and content that drives qualified traffic, enabling continuous optimization.
Using analytics tools enhances decision-making by linking website activity to business outcomes. Cybersecurity firms evaluate which content, keywords, or campaigns generate leads, refine strategies accordingly, and demonstrate ROI for SEO and marketing efforts, ultimately improving overall conversion rates and recurring client engagement.
26. Align SEO Goals With Marketing and Lead Generation Objectives
Aligning SEO goals with overall marketing and lead generation objectives ensures that cybersecurity firms drive targeted traffic that converts into qualified leads. SEO efforts should focus on attracting businesses searching for security solutions while integrating with email campaigns, paid advertising, and content marketing initiatives.
A coordinated strategy allows firms to connect keyword targeting, content creation, and link-building campaigns directly to specific lead generation outcomes. This alignment ensures that search engine visibility contributes to measurable business goals such as consultation requests, demo sign-ups, and service inquiries.
Mapping SEO metrics to marketing KPIs enables continuous evaluation of performance and resource allocation. Cybersecurity firms identify which pages, topics, or search queries deliver the highest ROI, refine content strategies, and optimize campaigns to increase conversions, ultimately improving recurring client acquisition and long-term revenue growth.
27. Engage With Cybersecurity Communities, Forums, and Professional Networks
Engaging with cybersecurity communities, forums, and professional networks establishes the firm as a credible authority in the security industry. Active participation in discussions, answering technical questions, and sharing insights attracts decision-makers seeking trustworthy cybersecurity services. This interaction increases visibility, drives targeted referral traffic, and indirectly improves search engine rankings through mentions and backlinks from industry-relevant sources.
Regular engagement allows firms to monitor emerging trends, identify pain points, and understand the evolving needs of potential clients. These insights inform the creation of specialized content, including service pages, guides, and case studies, which align with user intent and improve keyword relevance. Consistently contributing value allows the firm to strengthen relationships with partners, industry influencers, and professional peers, enhancing its reputation across multiple channels.
Cybersecurity firms benefit from measurable outcomes such as increased qualified leads, higher engagement rates, and improved brand authority. Strategic participation in forums and communities complements other SEO efforts, boosts organic reach, and reinforces trust, ultimately strengthening the firm’s goal of generating recurring business while maintaining thought leadership in highly competitive markets.
28. Measure Success by Qualified Leads, Client Inquiries, and Closed Deals
Measuring success through qualified leads, client inquiries, and closed deals provides a direct evaluation of SEO performance for cybersecurity firms. Tracking these metrics connects organic search efforts to tangible business outcomes, revealing which strategies generate the highest-value traffic and conversion opportunities. This method allows firms to prioritize high-impact SEO activities while minimizing resources spent on underperforming tactics.
Analyzing leads and inquiries identifies trends in searcher intent and highlights which content, keywords, and landing pages attract decision-makers. Cybersecurity firms segment data by service, region, or audience persona to refine campaigns and improve targeting accuracy. This approach ensures that the website aligns with client needs and conversion goals while maintaining technical and content optimization standards.
Continuous tracking of closed deals demonstrates ROI from SEO initiatives, proving the value of organic visibility in revenue generation. Regular performance measurement informs strategic adjustments, strengthens marketing alignment, and ensures that SEO contributes effectively to the growth, credibility, and market positioning of the firm.
29. Update, Consolidate, or Remove Outdated Content
Updating, consolidating, or removing outdated content maintains the website relevance of a cybersecurity firm and authority in search engines. Fresh, accurate content signals to search engines that the site provides current, trustworthy information, which enhances rankings for target keywords. Regular content audits identify pages with obsolete statistics, expired references, or duplicated topics that dilute SEO performance.
Consolidating multiple pages on similar topics improves user experience by reducing content fragmentation and strengthening topical authority. Merging overlapping content ensures that search engines index a single, comprehensive page rather than several thin or redundant pages. Removing irrelevant or low-value pages prevents wasted crawl budget and eliminates potential negative impacts on overall site performance.
Cybersecurity firms benefit from consistent content review cycles, which allow rapid adaptation to evolving threats, compliance standards, and industry trends. This practice preserves the credibility of a website with both users and search engines, improves engagement metrics, and maintains steady organic traffic growth, ensuring ongoing visibility and qualified lead generation.
30. Consider Expert SEO Support for Continuous Optimization and Growth
Engaging expert SEO ensures that cybersecurity firms maintain consistent optimization across technical, on-page, and off-page strategies. Continuous guidance from professionals strengthens website authority, improves search engine rankings, and sustains long-term organic traffic growth. Experts identify gaps, monitor algorithm changes, and implement advanced techniques that internal teams overlook.
Regular collaboration with SEO specialists allows cybersecurity firms to refine keyword targeting, enhance content quality, and track performance metrics effectively. Professionals execute strategic audits, optimize site architecture, and coordinate link-building initiatives, ensuring alignment with the business objectives and lead generation goals of the firm. Outsourced SEO expertise reduces errors in complex technical configurations and keeps the website competitive against evolving market conditions.
Cybersecurity firms that use expert SEO experience measurable benefits, including higher organic visibility, better-qualified leads, and improved conversion rates. Continuous optimization preserves authority, prevents ranking drops, and enables scalable growth while minimizing resource strain on internal teams, securing a resilient SEO foundation for recurring revenue and industry credibility.
Is SEO for Cybersecurity Firms as Important as It Is for Tech Companies
SEO holds equal importance for cybersecurity firms and tech companies because both rely on digital visibility to attract clients. Cybersecurity firms compete in a highly specialized niche where trust and authority drive conversions. Effective SEO builds search credibility, increases organic reach, and generates qualified leads from decision-makers seeking protection services. Without proper optimization, firms lose visibility to competitors with stronger digital presence and better search positioning.
How Long Does SEO Typically Take to Show Results for a Cybersecurity Firm
SEO progress for cybersecurity firms usually becomes noticeable within four to six months, depending on competition, technical structure, and content strength. Search engines take time to crawl, index, and evaluate domain authority.
Firms that implement comprehensive technical, on-page, and link-building strategies observe faster ranking improvements. Continuous updates, content expansion, and backlink acquisition strengthen credibility over time. Consistent optimization maintains ranking stability, ensuring lasting visibility in cybersecurity search segments.
Is Local SEO Enough for Cybersecurity Firms to Reach Nearby Clients
Local SEO assists cybersecurity firms in attracting regional businesses and government entities. However, relying solely on local optimization limits broader client acquisition. National and international visibility remains essential for firms handling enterprise-level security needs or compliance projects. Combining local and organic strategies ensures consistent growth across various market tiers.
Can a Cybersecurity Firm Provide Services to Clients in Other Countries
Cybersecurity firms serve international clients since most security operations occur remotely. Global SEO strategies with multilingual pages, localized content, and hreflang implementation improve visibility in foreign markets. Effective international targeting expands client reach while maintaining compliance with regional regulations and data protection standards.
How Can Cybersecurity Firms Use SEO to Attract Global Clients
Cybersecurity firms attract global clients by implementing an international SEO strategy focused on multilingual content, region-specific keywords, and local regulations. Creating localized landing pages for different regions builds trust and relevance. Using hreflang tags ensures that users in each country see the correct language version of the website, improving engagement and conversions.
Firms should also publish globally relevant thought leadership content, such as cyber threat intelligence reports and compliance insights, to build authority. Combined with high-quality backlinks from international publications, these efforts expand reach, enhance credibility, and position the cybersecurity firm as a trusted global partner.
Is Multilingual SEO as Important as Local SEO for Cybersecurity Firms
Yes, multilingual SEO is equally important because it allows cybersecurity firms to communicate expertise in the native language of clients, which builds trust and improves engagement. Local SEO targets nearby prospects, while multilingual SEO ensures visibility in international search results, allowing firms to compete effectively in global cybersecurity markets.
What Role Does Technical SEO Play in Optimizing a Cybersecurity Website
Technical SEO is vital for optimizing a cybersecurity website because it ensures search engines crawl, index, and interpret site content accurately. It includes optimizing site speed, security protocols, mobile responsiveness, and structured data. For cybersecurity firms, a technically sound website not only improves rankings but also demonstrates operational credibility, essential in a trust-driven industry.
Maintaining strong technical health prevents crawl issues, improves Core Web Vitals, and enhances user experience. In short, technical SEO provides the stability and trustworthiness needed for long-term visibility and lead generation.
Can Cybersecurity Firms Manage SEO on Their Own Without Experts
Cybersecurity firms handle basic SEO tasks internally, such as content updates or meta optimizations, but expert involvement ensures stronger results. Professional SEO specialists bring advanced knowledge of algorithms, keyword strategy, and technical optimization. For firms aiming to scale globally or dominate competitive niches, expert guidance ensures sustainable growth, higher ROI, and consistent visibility across target markets.
What Key Factors Should Cybersecurity Firms Consider Before Hiring an SEO Agency
Before partnering with an SEO agency, cybersecurity firms must evaluate several critical factors to ensure alignment with their goals, technical needs, and market positioning. The right agency should demonstrate not just SEO expertise but also a deep understanding of cybersecurity language, compliance standards, and client acquisition models. The factors to consider for cybersecurity firms before hiring an SEO agency are listed below.
- Industry Experience and Specialization: Choose an agency familiar with cybersecurity or IT markets. Understanding complex services such as threat intelligence, SOC management, or compliance frameworks ensures accurate keyword targeting and a relevant content strategy.
- Proven Case Studies and Performance Metrics: Review past campaigns, results, and client success stories. Look for evidence of ranking growth, lead generation, and technical execution tailored to high-security sectors.
- Technical SEO Expertise: Ensure the agency excels in technical optimization, secure site structures, Core Web Vitals, schema markup, and log analysis, critical for trust-driven cybersecurity sites.
- Transparency in Strategy and Reporting: The agency should provide clear, data-backed progress reports with transparent insights into KPIs such as organic traffic growth, domain authority, and conversion metrics.
- Alignment with Business Objectives: Select an SEO partner that understands long-term lead generation, B2B sales cycles, and authority-building goals rather than focusing solely on keyword rankings.
- Compliance and Security Awareness: Given the sensitive nature of cybersecurity, the agency should follow strict data privacy protocols and understand compliance frameworks like GDPR, ISO 27001, and SOC 2.
- Scalability and Ongoing Optimization: The agency should offer scalable SEO programs, adapting strategies as the firm expands into new markets or services.
Hiring the right SEO agency requires evaluating both strategic and technical fit. A well-aligned partner will enhance visibility, authority, and lead generation, enabling cybersecurity firms to grow securely and sustainably.
Which Agency Offers the Best SEO Services for Cybersecurity Firms Near Me
LinkGraph ranks as the best SEO agency for cybersecurity firms and a leading seo and marketing services provider for cybersecurity firms due to its specialised expertise, measurable results, and proven track record. The agency implements strategies tailored to cybersecurity firms, combining technical SEO, authority building, and content marketing to attract qualified leads and increase organic visibility. Case studies demonstrate organic traffic growth exceeding 100 % within months, while client testimonials highlight transparent reporting, strategic guidance, and measurable ROI.
LinkGraph addresses complex cybersecurity search intent, including compliance, threat mitigation, and incident response, ensuring high-value keywords align with target audiences. Their comprehensive services include technical audits, on-page and off-page optimization, backlink acquisition, and content creation specifically for cybersecurity brands.
Monthly performance dashboards allow firms to track keyword rankings, traffic, and lead generation effectively. Choosing LinkGraph provides cybersecurity firms with a results-driven SEO partner recognised for delivering measurable growth, industry-specific expertise, and strategies that directly impact online visibility and client acquisition.
How Much Does LinkGraph Charge Monthly for SEO Services for Cybersecurity Firms
LinkGraph’s monthly SEO services for cybersecurity firms start at $1,500 for small business plans and scale up to $12,000 for enterprise campaigns. Entry-level packages include foundational technical SEO, on-page optimization, and basic link-building. Mid-tier plans allocate additional resources to content creation, authority building, and custom reporting dashboards.
Enterprise plans deliver full-scale campaigns with high-authority link acquisition, advanced analytics, and dedicated strategic guidance. The pricing reflects the specialized requirements of cybersecurity firms, including competitive keywords, high-trust standards, and technical compliance considerations.
Investing in these services ensures improved search visibility, qualified lead generation, and measurable growth in recurring revenue. Each plan aligns SEO strategies with business goals, making the retainer a strategic investment rather than a simple marketing expense. This structured approach enables cybersecurity firms to achieve sustainable rankings and maintain credibility in a competitive market.
What Types of SEO Services Does LinkGraph Provide for Cybersecurity Firms
LinkGraph provides a full suite of SEO services tailored specifically for cybersecurity firms, designed to improve online visibility, drive qualified leads, and establish industry authority. Their services address every aspect of SEO, from technical optimization and on-page improvements to content strategy, link building, and reputation management. Each service is crafted to meet the unique needs of cybersecurity companies, ensuring measurable growth and sustainable search rankings.
The types of SEO services offered by LinkGraph to cybersecurity firms are listed below.
- Holistic SEO for Cybersecurity Firms: Comprehensive strategy covering all SEO facets to maximize visibility and ranking potential.
- Technical SEO for Cybersecurity Firms: Optimization of site speed, security protocols, crawlability, and structured data to enhance indexing.
- On-Page SEO for Cybersecurity Firms: Optimization of meta tags, headers, content, and internal linking to improve relevance and user experience.
- Content Strategy and Marketing for Cybersecurity Firms: Creation of authoritative, high-value content that addresses security challenges and buyer intent.
- Off-Page SEO for Cybersecurity Firms: Activities that strengthen domain authority through external channels and mentions.
- Link Building for Cybersecurity Firms: Acquisition of high-quality backlinks from reputable tech and industry websites.
- Local SEO for Cybersecurity Firms: Optimization to capture geographically relevant leads and appear in local searches.
- Reputation Management for Cybersecurity Firms: Monitoring and managing online reviews, citations, and brand mentions to maintain trust.
Each service aligns with the strategic goals of cybersecurity firms, delivering measurable impact in search visibility, lead generation, and long-term authority.
Which Types of Cybersecurity Firms Can Get SEO Services From LinkGraph
LinkGraph offers specialized SEO services for a wide range of cybersecurity firms, ensuring each type achieves improved online visibility, attracts qualified leads, and strengthens credibility within its niche. These services cater to firms of varying sizes, specialties, and operational models, adapting strategies to meet unique market demands and client requirements. The types of cybersecurity firms that benefit from SEO services provided by LinkGraph are listed below.
- Managed Security Service Providers (MSSPs): Firms offering continuous monitoring, threat detection, and response services benefit from targeted SEO strategies to reach enterprise clients.
- Network and Infrastructure Security Companies: Providers focusing on firewall management, VPN solutions, and secure network architecture gain visibility for technical search queries.
- Compliance and Risk Management Firms: Organizations specializing in regulatory compliance, audits, and risk assessment attract clients searching for HIPAA, GDPR, or ISO-specific solutions.
- Cloud Security Providers: Companies delivering cloud protection, encryption, and SaaS security optimize for high-intent keywords targeting cloud adoption and hybrid environments.
- Threat Intelligence and Incident Response Firms: Firms offering proactive threat analysis, cyber threat intelligence, and incident mitigation benefit from content-driven SEO and authoritative backlinks.
- Penetration Testing and Vulnerability Assessment Companies: Providers conducting ethical hacking and security assessments achieve a higher ranking through technical content and solution-focused pages.
These services ensure that cybersecurity firms across different verticals establish authority, attract qualified leads, and maintain competitive positioning in search results.
How Can I Hire LinkGraph for SEO Services for My Cybersecurity Firm
Hiring LinkGraph for SEO services for a cybersecurity firm involves a clear, structured process designed to ensure alignment with your business goals, target audience, and security niche. Each step focuses on understanding the needs of the firm, implementing tailored SEO strategies, and maintaining ongoing optimization to drive qualified leads and visibility in search results. The steps to hire LinkGraph’s SEO services for cybersecurity firms are listed below.
- Schedule a Consultation: Initiate contact with LinkGraph through their contact form or call to discuss the objectives of your cybersecurity firm and current SEO status.
- Conduct SEO Audit: Allow LinkGraph to perform a comprehensive audit of your website, analyzing technical issues, on-page optimization, content, and backlink profile.
- Receive Custom SEO Proposal: Review the tailored strategy and scope, which outlines recommended actions, timelines, and expected outcomes for your cybersecurity firm.
- Approve Strategy and Initiate Work: Confirm the proposed plan and begin the SEO implementation process, including technical fixes, content creation, and link-building campaigns.
- Ongoing Monitoring and Optimization: Track performance through analytics, adjust strategies based on results, and maintain continuous growth for long-term visibility and lead generation.
Following these steps ensures cybersecurity firms engage LinkGraph efficiently while maximizing SEO effectiveness and ROI.

